
Single-sign-on (SSO) is a must for any efficient team. The idea is that you require just one login to access all systems and devices that you have been granted user rights. There are various providers that make this process easy and secure. Zammad currently supports SSO via SAML, OpenID Connect and Shibboleth.
Efficient Single Sign-On Options
What if there was an easy way to quickly sign in to all your devices and systems without having to remember countless passwords? Oh but there is! SAML, OpenID Connect and Shibboleth have been created purely for this purpose – and you can now use them for your Zammad instance.
Related blog post:
How Single Sign-On secures your helpdesk and saves your team time
SAML
SAML (Security Assertion Markup Language) is an open standard for SSO authentication (among other things). Sign-ins are shared across multiple service providers and managed by a central identity provider (IdP).
In this case, the service provider is Zammad, and the IdP is a software service that you either host or subscribe to (e.g., Keycloak, Redhat SSO Server, ADFS, or Okta).
Setup
In order to use SAML for Zammad, follow these steps:
- Add Zammad as a client/app in your IdP
- Set up user attribute mapping
(email address, full name, given name, and family name) - Add Per-IdP instructions to Zammad
- And finally, configure your SAML authentication in Zammad
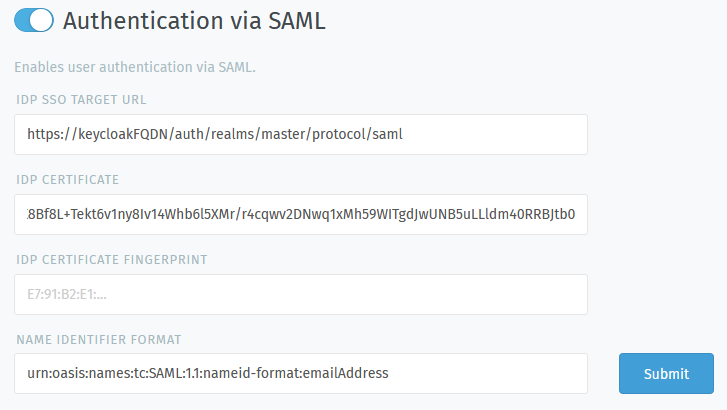
For more details, check out the Admin documentation.
OpenID Connect
As of Zammad 6.5, OpenID Connect can be used as a Single Sign-On (SSO) method – for example, via Keycloak or any other compatible OpenID provider.
In this setup, Zammad acts as the Relying Party (RP), while the OpenID provider serves as the identity service. This enables centralized user management and provides a seamless login experience for your entire team.
Benefits:
- Single Sign-On using your existing OpenID provider
- Unified authentication for all users
- Automatic logout when the session ends
- Increased security and reduced administrative effort
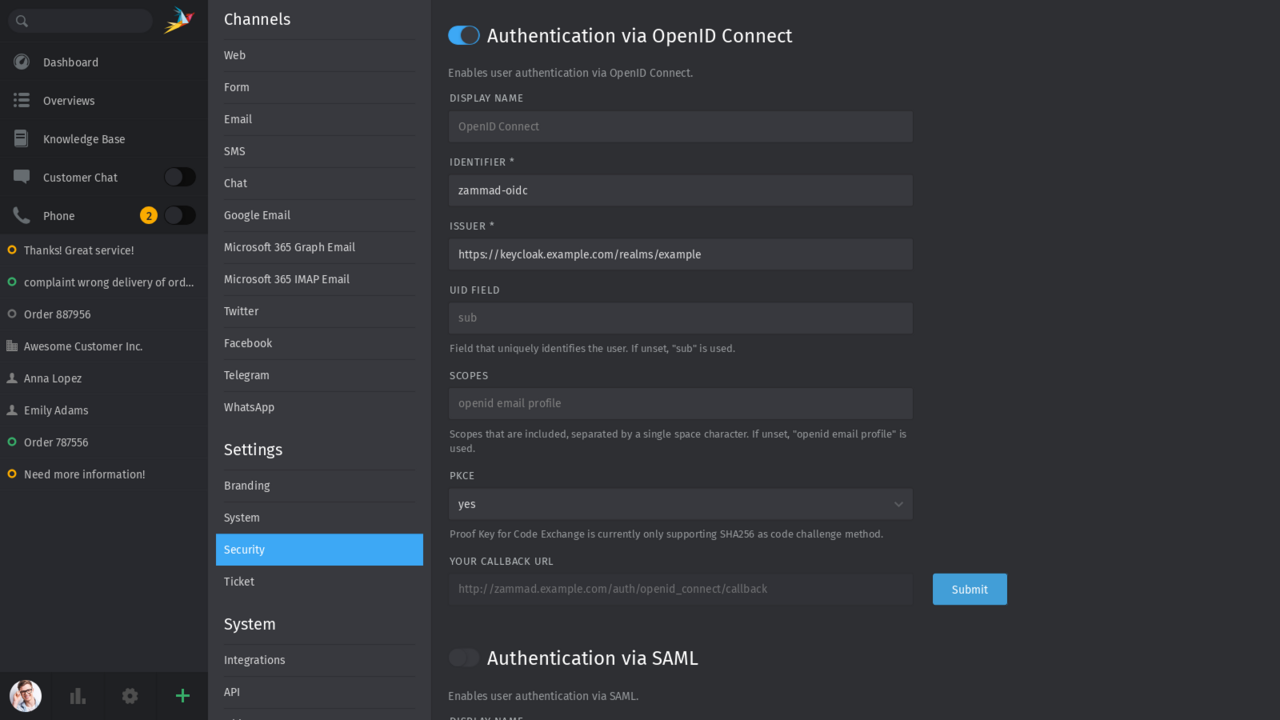
🛠️ OpenID Connect setup in the Zammad Admin Documentation
💛 This feature was made possible thanks to the generous support of the Ostfalia University of Applied Sciences – thank you!
Shibboleth
Shibboleth has been a popular open-source identity management software since the early 2000s. If you are already using it, you can connect it to Zammad, similarly to SAML.
Simply configure Shibboleth for the Zammad IdP and initiate the authentication. There is no documentation for this yet, so just let us know if you need help!