What this post is about
- Why vulnerability management matters for all organizations
- How open source brings enterprise-grade security to SMEs
- A real-world pipeline using Greenbone, n8n, Zammad, and Discord
- Practical insights from building and running the system
Why Vulnerability Management Matters
No IT environment is immune to vulnerabilities. Outdated applications, unpatched systems, and insecure third-party integrations can expose a network to potential threats. Even a missed update or minor misconfiguration can give attackers the opportunity to exploit weaknesses.
For small and medium-sized businesses, a single breach can cause enough disruption to result in operational downtime, data loss, compliance issues or long-term reputational damage. This is why I see vulnerability management as a proactive shield rather than a reactive fix. Automation, traceability and speed are crucial for early vulnerability detection, assigning responsibility and resolving issues efficiently with full transparency at every step.
The Open Source Advantage
Traditional vulnerability management solutions often come with complex licensing terms, high costs, and a steep learning curve. However, many of today's most flexible and powerful tools are open source. These tools are maintained by active communities and are suitable for organizations of any size.
In fact, open source does more than just save costs. To me, it is a strategic choice that enables autonomy. Teams can adapt their security operations center (SOC) pipelines as the business evolves without being locked into a vendor’s ecosystem or having to compromise on functionality.
💡 Why Open Source Matters at Zammad?
Zammad is proudly open source — and always will be. That means full transparency, community-driven development, and the freedom to adapt the software to your needs. No vendor lock-in. No hidden costs. Just a helpdesk platform that grows with you.
The Architecture: Four Tools Working in Harmony
In my setup, the entire vulnerability management pipeline is powered by open source software. Each tool plays a specific role, ranging from detection and automation to ticketing and alerting.
The core components include:
- Greenbone/OpenVAS for vulnerability scanning
- n8n for workflow automation
- Zammad for ticket creation
- Discord for team notifications
By keeping the architecture modular and lightweight, modifications can easily be made later. Future extensions, such as dashboards, asset inventory integrations, or external threat intelligence feeds, can be added as needed.
How It Works: A Step-by-Step Breakdown
At the heart of this solution is a modular automaton, orchestrated through n8n and interlinked with best-of-breed open source tools. Here’s an inside look at how the end-to-end flow works in practice:
1. Vulnerability Scanning with Greenbone/OpenVAS
The process starts with Greenbone/OpenVAS, a well-established open source scanner monitoring network assets. Each scan returns a comprehensive CSV report, complete with CVE identifiers, severity scores (CVSS), affected hosts, and recommended remediation strategies.
2. Automated Processing and Filtering with n8n
Instead of handling these reports manually, automation takes over. OpenVAS exports its scan as a CSV, which is parsed by a dedicated Python script acting as a proxy. This script transforms the CSV into JSON, which is then sent via webhook to n8n, where the real orchestration starts.
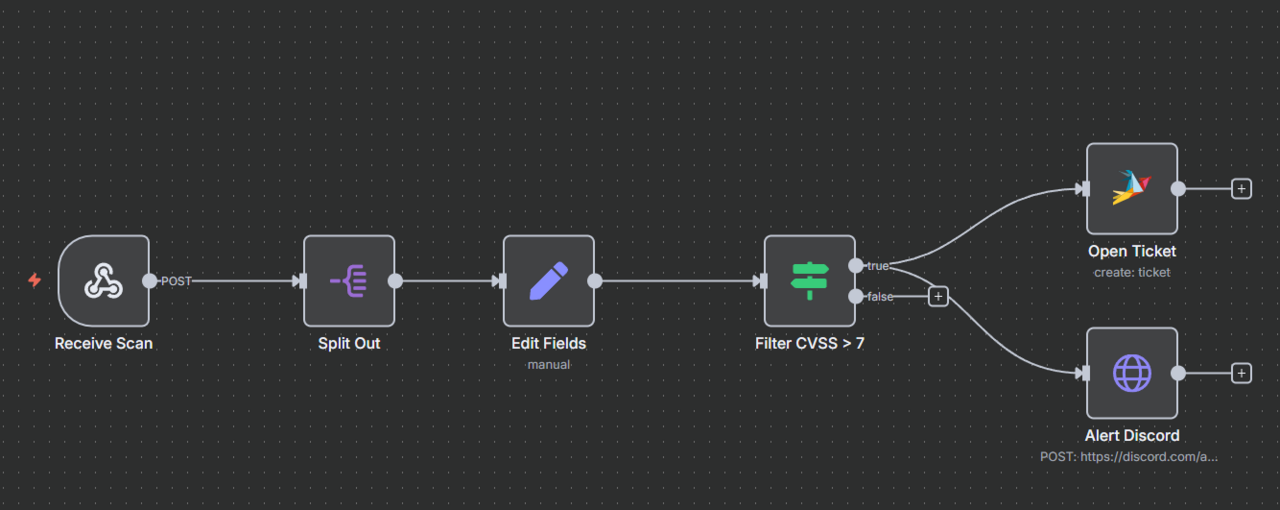
Inside n8n, the workflow follows an efficient sequence:
-
Webhook Trigger: As soon as the report arrives, the webhook node acts as the entry point, kicking off the entire process.
-
Splitting and Field Mapping: The raw data is split into individual vulnerabilities to ensure that each one is handled as a separate pipeline item. The "Set" node then extracts and maps the essential fields. This step standardizes the data and makes field management robust to changes in report formats.
-
Criticality Filtering: dedicated filter node evaluates each vulnerability’s CVSS score and allows only those above a defined threshold (e.g., >7) to proceed. This ensures that only high-risk issues demand analyst attention and trigger follow-up actions.
-
Standardized Message Generation: With clean, filtered data, the workflow generates structured, readable summaries for all subsequent steps.
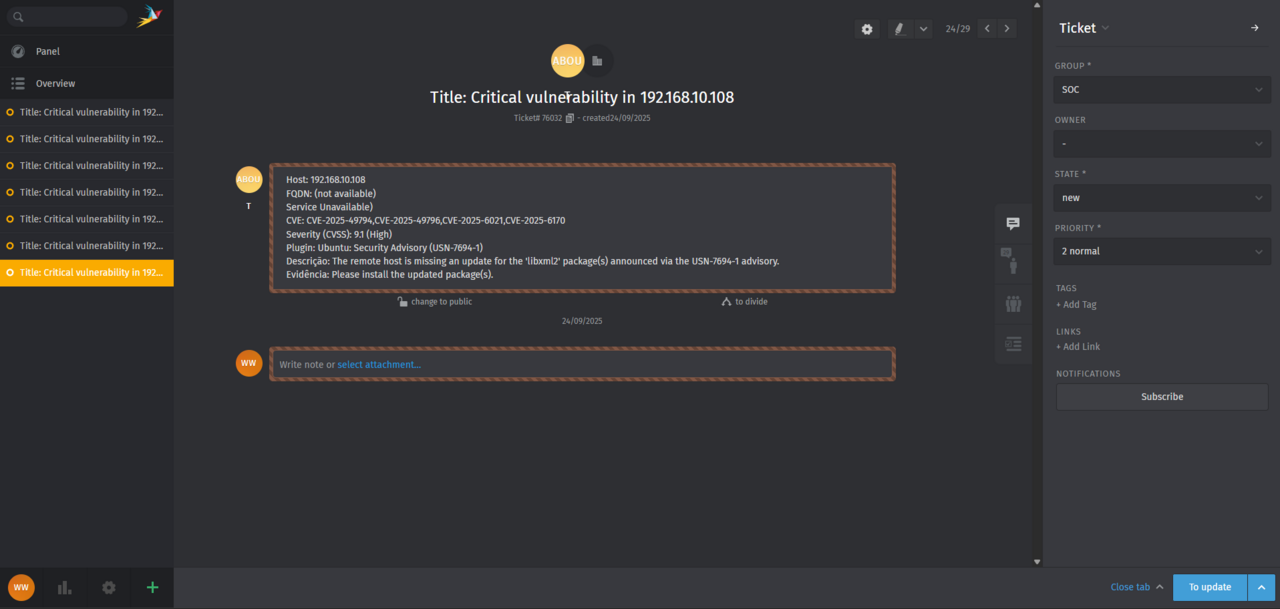
3. Automatic Ticket Creation in Zammad
The automation instantly triggers ticket creation in Zammad for every vulnerability that passes the severity filter. Each ticket contains all the critical details an analyst needs.
This process eliminates manual entry errors and ensures consistent follow-through. Zammad’s flexible tags, triggers, and group assignment features make it easy to prioritize, track, and escalate tickets based on business requirements.
The body content is formatted with line breaks and basic Markdown to make tickets readable and immediately actionable, helping analysts quickly understand the issue at hand.
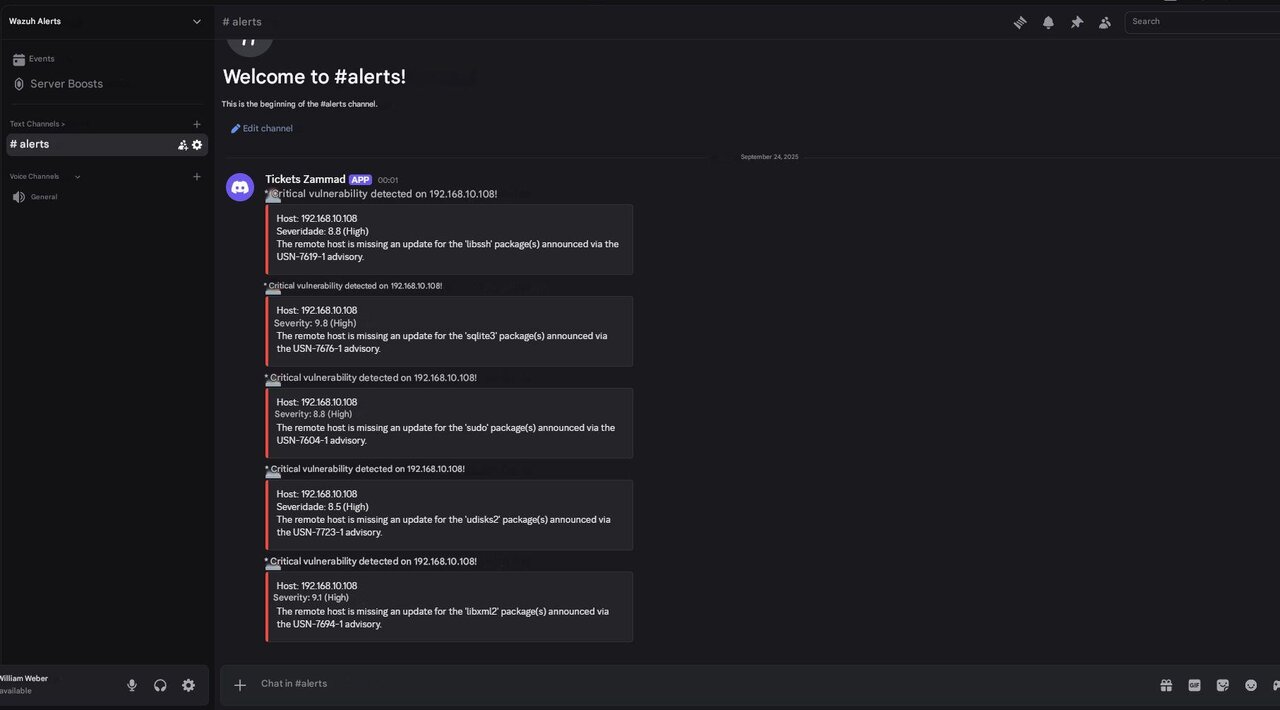
4. Real-Time SOC Alerts via Discord
Real-time awareness is crucial in fast-paced IT environments. As soon as a ticket is generated, a Discord notification is sent to the SOC team's channel via webhooks.
These alerts use color-coded embeds and structured Markdown formatting, ensuring high-priority risks are impossible to miss and prompting immediate action.
Measurable Results and Real-World Impact
The result is a streamlined, fully automated vulnerability management pipeline that dramatically improves speed and clarity. What used to take hours now happens in seconds. Critical vulnerabilities are automatically detected, triaged, and escalated. Standardized Zammad tickets provide SOC analysts with all the necessary information upfront, and real-time Discord alerts ensure that high-severity issues receive immediate attention.
Every step is traceable, from detection to resolution, creating a reliable audit trail that supports compliance and continuous improvement.
With no licensing costs or vendor lock-in, this setup is also cost-efficient. Self-hosted, open-source tools make enterprise-grade processes accessible, scalable, and affordable for small- and mid-sized teams.
Next Steps: Scaling and Advancing the Pipeline
The system already lays a robust foundation, but there’s plenty of room for expansion, for instance:
-
Ticket Deduplication: Adding a step to check Zammad for existing tickets based on CVE and IP would prevent duplicates and instead append updates, improving signal-to-noise for analysts.
-
External Enrichment: Incorporate live threat intelligence APIs (such as CISA’s Known Exploited Vulnerabilities Catalog after filtering, allowing the team to prioritize truly active threats.
-
Metrics and Dashboards: Integrate with a platform like Grafana, using data from OpenVAS and Zammad, to visualize remediation metrics (e.g., mean time to remediation, open vulnerabilities by severity).
-
Remediation Automation: For recurring, low-risk issues, automatically trigger playbooks (e.g., via Ansible) to patch vulnerabilities without human intervention.
Getting Started
If you're looking to build a similar pipeline, my advice is to start simple and expand gradually. First, connect your vulnerability scanner, ticketing system, and team messaging channel. Then, as your needs grow, add filtering, notification features, and more sophisticated data transformation.
All of these tools are free to use, well-documented, and supported by active communities. You don’t have to build perfection from day one. Just take the first step.
If you're already using Zammad, you've got the perfect foundation for bringing all the pieces together.

